
General installation instructions for CAPTCHAv2
Last Updated: 2009-07-06
Installation CAPTCHAv2 is pretty simple, this guide will cover correct file placement, initial configuration and table creation via the install script.
Please download the latest edition before you continue.
CAPTCHAv2 is designed so it can be installed into any directory of your website and different programs can share a common question,answer and IP cache database tables or use their own.
This installation guide will assume that
1) your website is http://www.localhost.local and that you copied the CAPTCHAv2 files into the captchav2/ directory (http://www.localhost.local/captchav2/).
You can choose another directory as long as you don't overwrite any existing files.
2) Use your web browser and open the CAPTCHAv2 directory (http://www.localhost.local/captchav2/)
3) Follow the installer instructions, pay special attention to the abuse.php path option. The default is only correct if you installed CAPTCHAv2 into (http://www.localhost.local/captchav2/)
4) Login to CAPTCHAv2 and add your own questions. The management page is self explaining so I will not cover it for now. Here is a screenshot: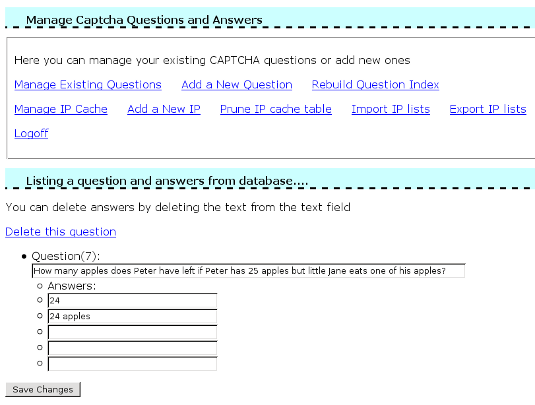
Explanation of configuration values in config.php
The information below will explain the different option in config.php and here as a reference but should not be needed since the installer created the file for you.
- $debug => This option allows you to specify if you would like to see debug messages. Note that the debug emails will only be sent out if $email_notifications is set to true. WARNING Debug option 2 is verbose! It will output the debug message to the screen for all to see!
Example debug outputThis is a debug notice from class_captcha.php
An answer to the CAPTCHA was provided and will be validated
Question ID: 3
Solution (escaped for SQL): #file_links[c:\\xrum\\files\\acai\\hublinks.txt,1,n]
User IP: xxx.xxx.xxx.xxx
User Agent: Mozilla/1.22 (compatible; MSIE 2.0; Windows 95)
The following SQL query will be executed to validate the solution.
SELECT question_id FROM captcha_answers_eng WHERE question_id = 3 AND answer = '#file_links[c:\\xrum\\files\\acai\\hublinks.txt,1,n]' LIMIT 1 - $failed_max_attempts => This option specifies after how many failed attempts the IP is added to the .htaccess file
- $email_notifications => Set this to true to receive notification emails.
$email_notifications = true;
Example emailAn invalid answer to the CAPTCHA was provided The IP has been added to the captcha_invalid table but has not been
Here is another
blocked yet.
Question ID: 3 Solution (escaped for SQL): #file_links[C:\Xrum\Files\acai\hublinks.txt,1,N]
User IP: xxx.xxx.xxx.xxx
User Agent: Mozilla/1.22 (compatible; MSIE 2.0; Windows 95)About to add an IP to the htaccess file IP: xxx.xxx.xxx.xxx
Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.0.3705; .NET CLR 1.1.4322) - $email_errors => Set this to true to receive errors via email.
$email_errors = true;
Example emailFatal Error: Unable to open file /srv/http/.htaccess, please check permissions Script execution terminated by die();
- $email_to => This is where the notification and error emails are sent to
$email_to = 'user@domain.com';
- $invalids_lockout_time => Time in minutes until invalid login attempts are removed from the table. This number should be large, default 30 days, because some sneaky bots will submit one or two solutions to the CAPTCHA then try again a couple of days later.
- $blocklist_cache_clean_time => Time in minutes until a cached IP is removed from the table. This is done from the management interface (Prune IP cache table).
- $whitelist => This option contains words which will prevent an IP from being added to the blocklist. This feature works by asking a whois server for the record belonging to an IP. It will then attempt to find the whitelisted words on the whois record and prevent the IP from getting written to the .htaccess file if found.
No Comments yet .....
Add Your Comment:
Note: All posts require administrator approval. Please allow 24 hours for message approval.

